一款小巧简单的DDOS监测工具DDOS_Monitor (windows平台下),可以用来检测判断网络状态,不需安装,直接解压缩使用。
下面是说明文档
———————————————–
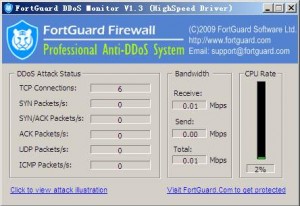
FortGuard DDoS Attack Monitor ver 1.3
. True green software, no need to install.
. The best tools to monitor and analyze DDoS attacks.
System Requirements:
Microsoft Windows 2000/2003 Server
Have you ever encountered the following situations?
. Your website access is suddenly very slow or even unreachable
. Your online game players disconnected all of a sudden
. inetinfo.exe, w3wp.exe or database process made CUP occupation rate very high
If the hardware problem could be excluded, you are probably facing DDoS attack! How to verify, monitor and analyze the attack? Run FortGuard DDoS Attack Monitor and check first!
On the common sense,
. SYN Packets/s > 100: SYN Flooding attack.
. ACK Packets/s > 500: ACK Flooding attack. (But for the downloading website, ACK Packets/s could possibly get to more than 1000)
. ICMP Packets/s > 50: ICMP Flooding attack.
. UDP Packets/s number is small while bandwidth occupation is high: UDP Flooding attack possibly.
. CPU occupation rate is more than 80%, and it is mostly caused by inetinfo.exe, w3wp.exe or database process: Vicious TCP Flooding attack.
FortGuard DDoS firewall can protect against all attacks above.
FortGuard DDos Protection
FortGuard provides the most reliable and fastest DDoS protection for online enterprises, public & media services, essential infrastructure and Internet service providers. Under attack? Please feel free to contact us.
MSN SalesOnline win@fortguard.com (Winston)
Technical Support support@fortguard.com
Copyright(C)2003-2009 FortGuard Software Technologies Ltd. All rights reserved.
down from www.xdowns.com
———————————————–
点此下载:DDOS_Monitor (211K)

0 条评论。